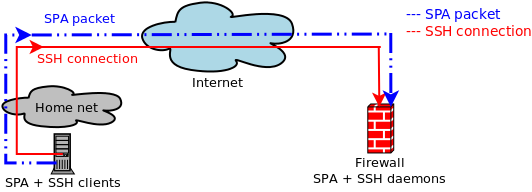
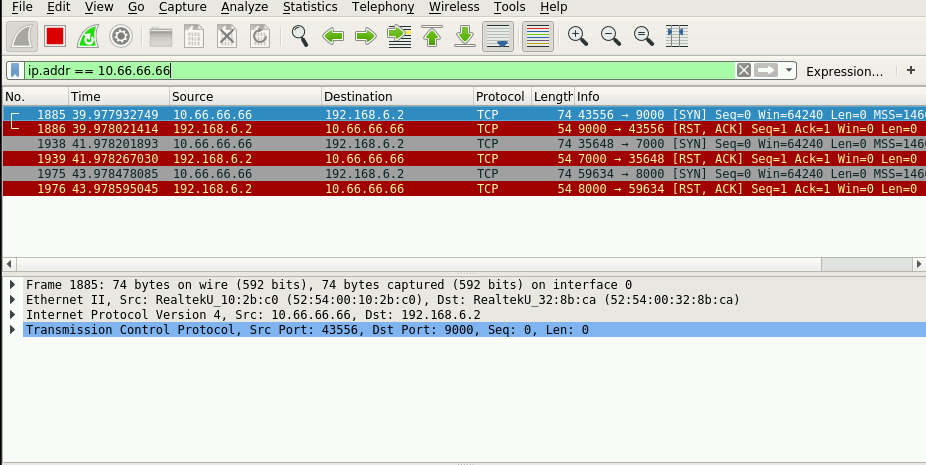
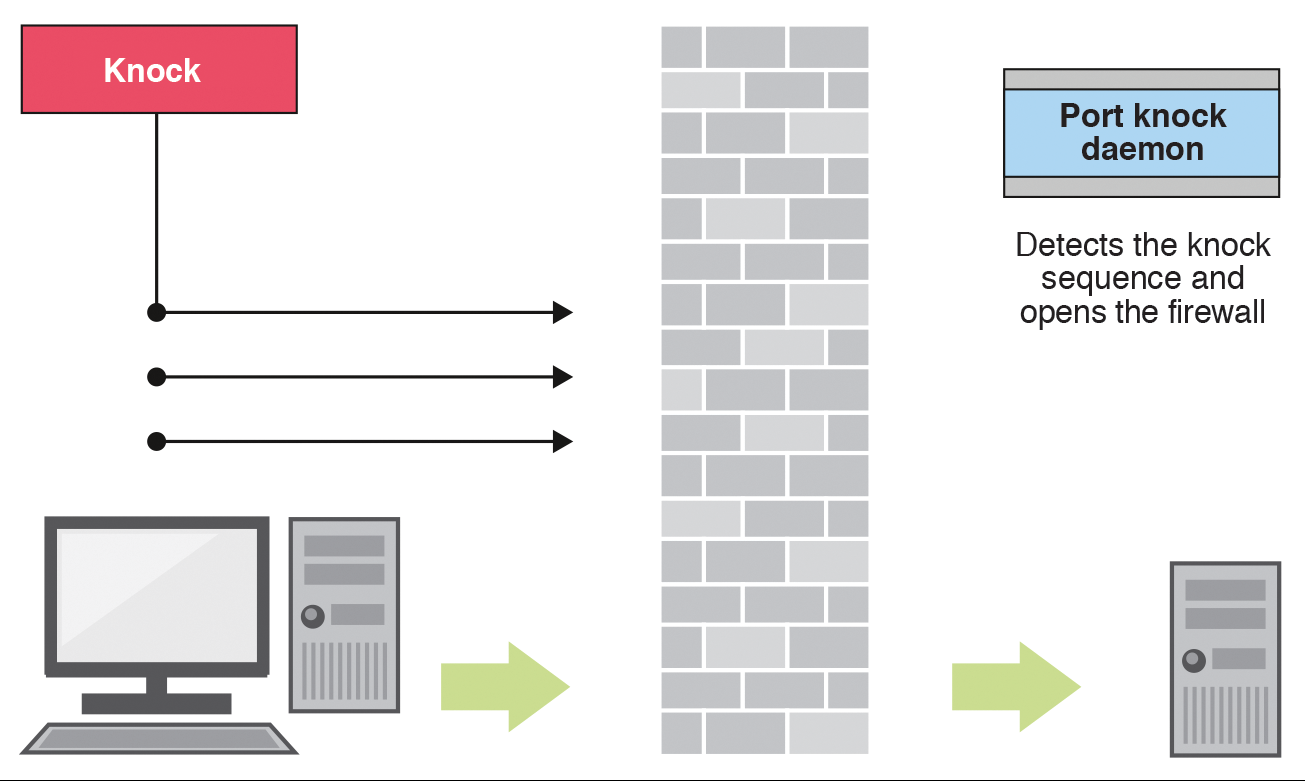
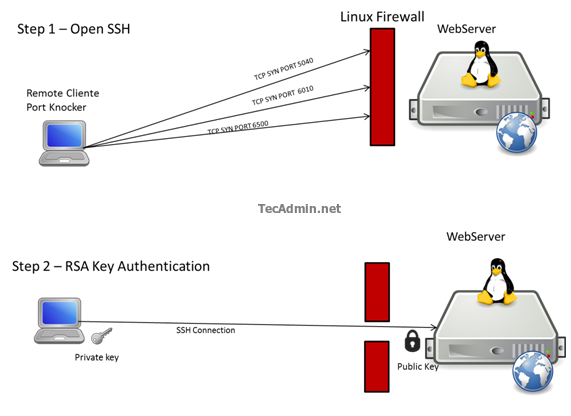
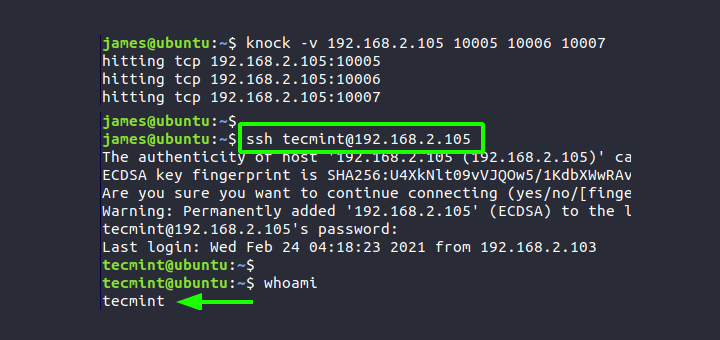
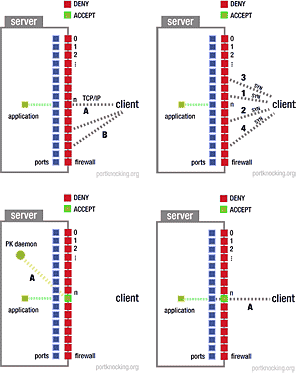
Port knocking example. The firewall is opened in response to a specific... | Download Scientific Diagram

شبكة الأمن المعلوماتي - شكون يعرف تقنية Port Knocking؟ واش بغيتو شرح عليه ولا شرح اخر؟ رأيكم في التعليق🙂 #شبكة_الأمن_المعلوماتي | Facebook

Figure 4 from Simple port knocking method: Against TCP replay attack and port scanning | Semantic Scholar







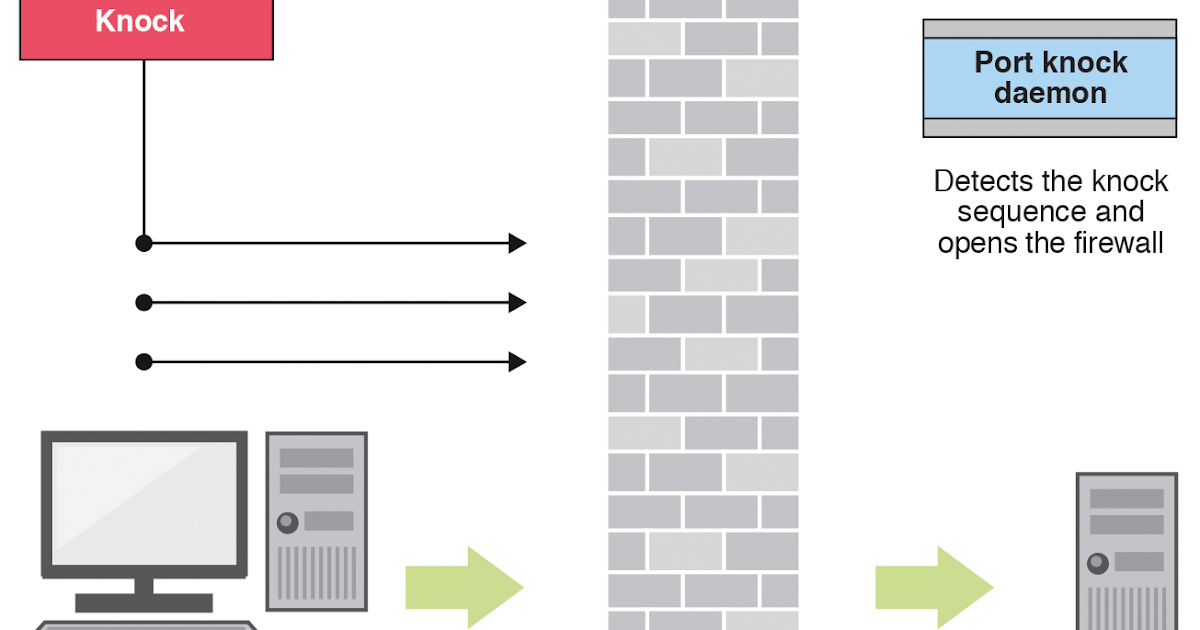
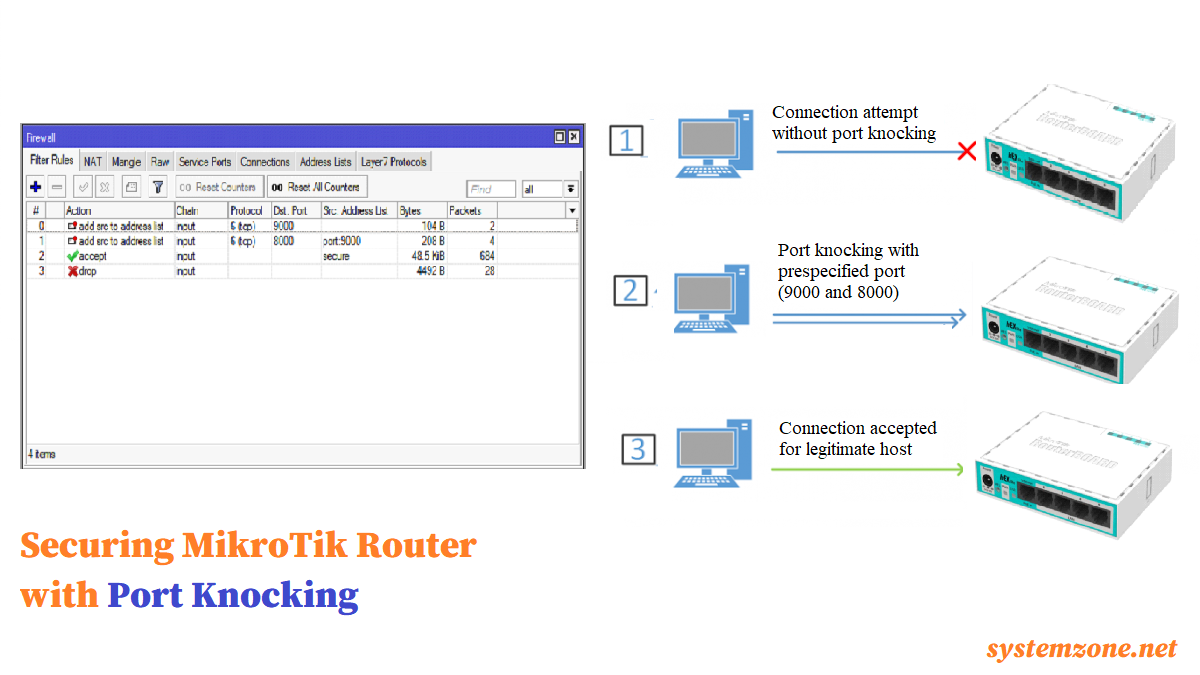
![minipost] Mikrotik/RouterBoard port-knocking example for firewall/NAT openings – NetworkGeekStuff minipost] Mikrotik/RouterBoard port-knocking example for firewall/NAT openings – NetworkGeekStuff](http://networkgeekstuff.com/wp-content/uploads/2014/06/Mikrotik_port_knocking.png)